WetStone
Industry Leader in Cyber Security and Computer Forensics Solutions
Delivering Insight and Efficiency to Cyber Crime Investigations
Since 1998, WetStone has developed software solutions that support investigators and analysts engaged in cyber-crime investigations, digital forensics, and incident response activities.
Gargoyle Investigator™ MP
Gargoyle Investigator™ MP is the next generation of WetStone’s advanced malware discovery solution for computer forensic investigators and incident response teams. It is designed for forensic laboratories, law enforcement, field investigators, advanced private investigators, and enterprise cyber security personnel. Gargoyle performs a rapid search for malicious applications and provides significant clues regarding the activities, motives and intent of a suspect.

Gargoyle Investigator™ MP takes everything that its current users know and love about Gargoyle Investigator and improves upon it. Its new, modern codebase, faster scan times, and improved archive and file format processing make Gargoyle Investigator™ MP a great improvement over the previous generation of Gargoyle Investigator™.
Gargoyle MP is designed to simplify your breach and malware triage investigation and incident response activities. Gargoyle MP enables users to perform a rapid search for known contraband, hostile programs and lost or leaked corporate assets.
Understanding the impact of malicious code is essential when conducting cyber crime investigations, whether it is the discovery of botnets, trojans, anti-forensics, mobile malware or a host of other malicious applications. Accessing the full intent, sophistication, capabilities and communications of cyber criminals requires a complete understanding of what is in play.
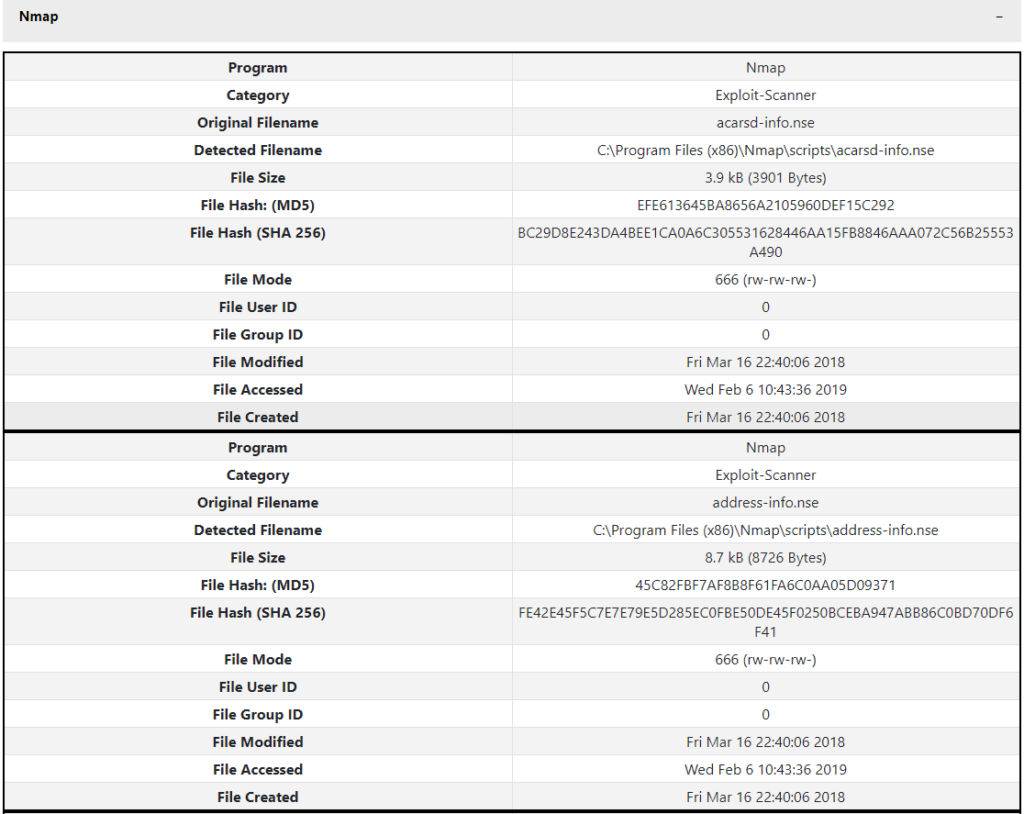
Gargoyle MP is designed to integrate with EnCase by Guidance Software and AccessData’s Forensic Toolkit (FTK) to streamline the process of performing investigations on live machines or forensic images. Users can utilize a WetStone Technologies-provided EnScript inside EnCase in order to create a hash file of all files present on an image. This hash file can then be used for advanced malware discovery using Gargoyle MP.
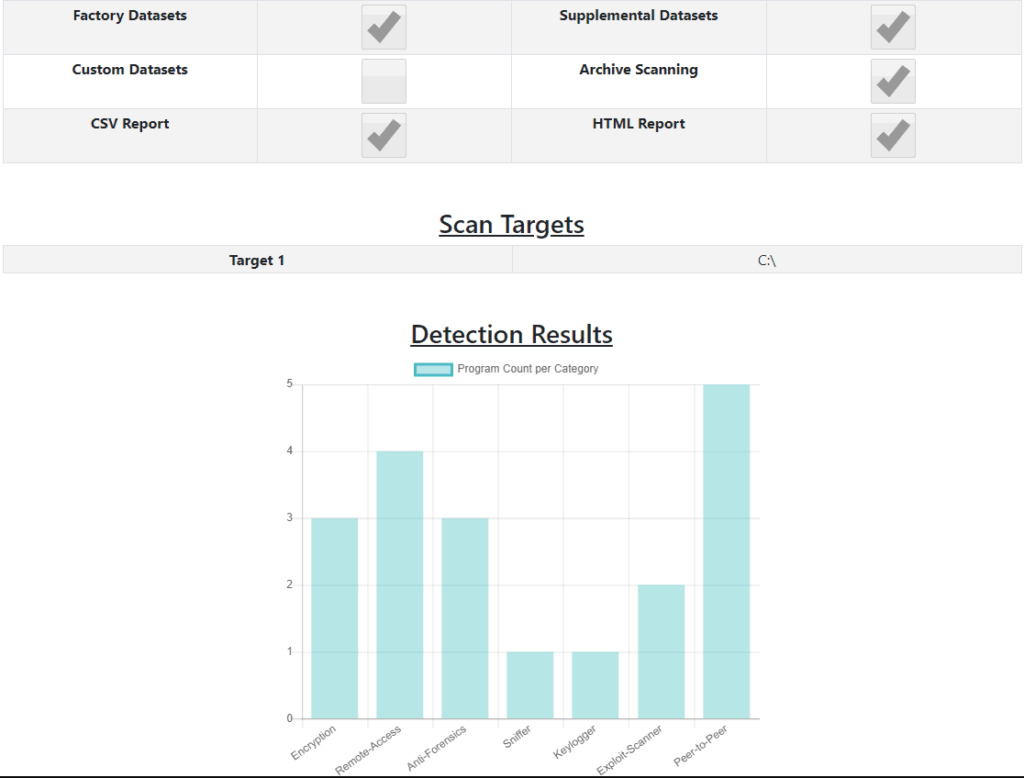
Gargoyle MP provides comprehensive reporting in both HTML and CSV formats for use as digital evidence. Reports are generated in HTML format for an at-a-glance understanding of the threats identified on a system. Within the HTML report program detections are classified by program category, with a comprehensive table of pertinent information provided for each detected file. Gargoyle also produces a CSV report, with all the same detection data, for use in parsing engines or other custom applications.
Gargoyle MP also gives users the option to generate a case file at the time of the scan. When selected, the program will generate a CSV file in the same format as the WetStone EnScript file. This gives the user the ability to re-scan a system later in the future.
FEATURES OF GARGOYLE INVESTIGATOR™ MP
• Advanced malware discovery
• Used by forensic labs, law enforcement, field investigators, private investigators, and incident response teams
• Rapid search of malicious applications
• Comprehensive reporting
Compatible with a variety of Windows desktop platforms:
o Windows XP
o Windows Vista
o Windows 7
o Windows 8
o Windows 8.1
o Windows 10
Compatible with a variety of Windows Server platforms:
o Windows Server 2003
o Windows Server 2008 and 2008 R2
o Windows Server 2012 and 2012 R2
o Windows Server 2016
Compatible with a variety of Linux platforms:
o Ubuntu 14, 16, 18
o Red Hat Enterprise Linux 7
o Fedora 29
o CentOS 7
o Debian 9
o Kali Linux
WHAT TYPES OF PROGRAMS CAN GARGOYLE MP DETECT?
• Peer-to-peer
• Piracy
• Ransomware
• Remote access
• Rootkit
• Scareware
• Sniffer
• Spyware
• Toolkit
• Trojan
• Web threats
• Wireless tools
• Anti-forensics
• Botnet
• Cryptojacking
• Cryptomining
• Denial of service
• Encryption
• Exploit Kit
• Exploit scanner
• Fraud tools
• Keylogger
• OSINT
• Password cracking
DELIVERABLE
LICENSING TYPES
• Your choice of either Electronic Software Download (ESD) or FLASH license type (USB device) for Gargoyle MP
• Access to monthly Dataset updates
• Customer support portal account
• 1-year software maintenance
• ESD: Electronic software download for use on a single system.Available as a perpetual or subscription license. Not transferable. Basic license is 2 cores, additional core licensing available.
• FLASH: 16GB USB 3.0 device for use in field investigations, and on multiple systems. Limited to 2 cores.

For more information please contact MergenPro’s sales team on info@mergenpro.com
StegoHunt™
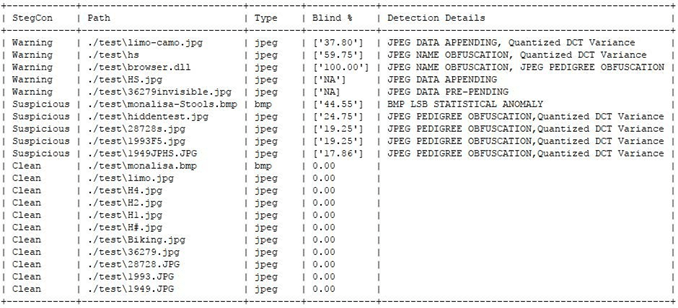
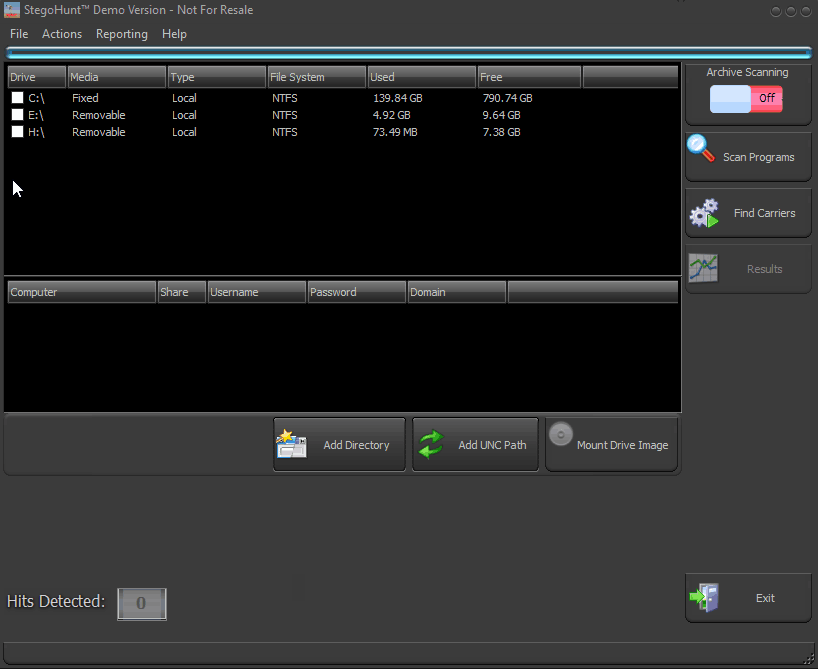
StegoHunt is an industry-leading steganography program discovery tool and steganalysis suite. StegoHunt effectively detects the presence of both data hiding programs and the files in which data may have been hidden (carrier files). It provides digital investigators, corporate auditors, incident response teams, and data loss prevention (DLP) experts with an easy-to-use suite of software tools that can identify data hiding programs on a system or forensic image, as well as to detect possible carrier files. A carrier file is used to conceal a digital payload using techniques that make it appear indistinguishable from the original version of the file.

After potential carrier files have been identified by StegoHunt, digital forensic analysts can advance the investigation by leveraging the powerful analytical capabilities of StegoAnalyst to view important characteristics of the carrier file. Steganalysis techniques, such as viewing file attributes, discrete cosine transform (DCT) coefficients and RGB color values provide clues that the investigator can use to identify the data hiding method being employed.
StegoBreak provides digital investigators with a tool to help break the encryption used by many data hiding programs. StegoBreak will launch a dictionary attack against the encryption and, if successful, allow the investigator to view the payload.
FEATURES OF STEGOHUNT™
• Identify the presence of carrier files on a system through statistical analysis techniques
• Identify the presence of data hiding tools and artifacts on a system
• View data about images, such as the bitmap, and utilize color filters for more information
• Crack and extract payloads from carrier files using encryption by launching a dictionary attack against the data hiding password
Included in this suite of tools
StegoHunt™
StegoAnalyst™
StegoBreak™


• Quickly identify if steganography is present in your investigations by scanning for over 1,000 data hiding applications using advanced, fast search methods
• Identify suspect carrier files that otherwise go undetected, including program artifacts, program signatures, and statistical anomalies
• Generate case-specific reports for management or court presentation
• Utilize multiple operational discovery modes, including directory, drive, archives, drive image, and network path
• Steganography analysis tool that provides deep investigation of detected images and audio files
• Utilize the file viewing panel to display the individual file attributes, including image details, discrete cosine transform (DCT) coefficients, and color pairs
• Select from various filter options for further presentation and analysis, such as least significant bit (LSB) of specific colors.
• Quickly and easily crack and extract payloads from many carrier files using a simple point and click interface
• Leverage the popular password dictionaries included in order to execute a dictionary attack
• Easily bring in other dictionaries, as well as create your own, to expand your dictionary attack
DELIVERABLE
LICENSING TYPES
• StegoHunt: Your choice of either Electronic Software Download (ESD) or USB Flash Drive (Flash) license type
• StegoAnalyst: Electronic Software Download (ESD) only
• StegoBreak: Electronic Software Download (ESD) only
• Access to monthly Dataset updates
• Customer support portal account
• 1-Year maintenance
StegoHunt is available in both electronic software download and flash licensing types. The electronic software download is an application that is licensed for installation on a single machine, such as a forensic workstation, and the license is non-transferrable. The flash StegoHunt license is a physical USB token that is provisioned to be used on many different systems. The StegoFlash™ token is useful if you have many different machines that you would like to analyze for the presence of data hiding artifacts and carrier files.
For more information please contact MergenPro’s sales team on info@mergenpro.com
StegoCommand™
StegoCommand is a command line Linux application that scans specified directories containing files to examine, and generates a report for each scanned file. StegoCommand is simple to use and requires a minimal amount of technical knowledge. StegoCommand builds upon the capabilities of the industry-leading Steganography discovery and analysis software tool, StegoHunt. Like its Windows-based predecessor, StegoCommand uses a collection of detection algorithms to quickly identify the presence of steganography in suspect carrier files.

Use cases for StegoCommand include: acceptable use policy enforcement, forensic investigations, data breach response, data leak analysis, insider threat identification, and mobile device examination.
StegoCommand supports several “out-of-the-box” file types for scanning for the presence of steganography. In addition to the “out-of-the-box” file types offered, the WetStone Technologies research and development team can work directly with a customer to expand the capabilities to scan for steganography in unique, custom, proprietary or industry-specific file types.
StegoCommand has the ability to traverse an unlimited number of nested archive files. Nested archives are often used in an attempt to conceal the presence of data hiding. With StegoCommand, users can be assured that all files in an archive file will be analyzed for the presence of hidden data.
FEATURES OF STEGOCOMMAND™
StegoCommand reports on the following data hiding techniques:
• Statistical anomalies
• Structural anomalies
• The presence of misplaced binary or UTF-8 data
• Data appending
• Data prepending
• File name obfuscation
• The presence of unusual Unicode data
• Comprehensive reporting
• Easily deployed to either on-premise or cloud-based environments
• Scalable to support analysis of very large files and very large data repositories
• Invoked via a command prompt or PowerShell
FILE TYPES SUPPORTED
• JPEG
• GIF
• BMP
• PNG
• ASCII (txt, csv, xml and html)
• Archive Files (includes but not limited to ZIP, TAR, JAR, APK, BZ2)
• HDF5
• NetCDF4
• BUFR
• NEXRAD
• HDF4
• HSD (Himawari)
SUPPORTED PLATFORMS
• Ubuntu
• Red Hat Enterprise Linux version 7
WetStone Technologies can work directly with a customer to support additional operating systems.
SYSTEM REQUIREMENTS
Computer system or virtual machine must meet or exceed the minimum requirements of 4GB RAM and 4 Core Processor.